
Critical Technologies is striving for one common goal that we call Trustworthy Network Autonomy. In the future Artificial Intelligence (AI) and Machine Learning (ML) will rule our software world. We see this future as one where these algorithms and systems evolve over time, changing in unforeseen ways by their creators. This is coming incredibly fast and terrifies us (as many don't seem to understand the consequences of such a new world) so we are working towards ways to safely live in peace with these new machines. This has lead Critical to develop the technologies of DAM3ON and SABLE, along with use seL4 and Genode to secure mixed-criticality systems, to create a foundation of trust that is open source and formally verifiable.

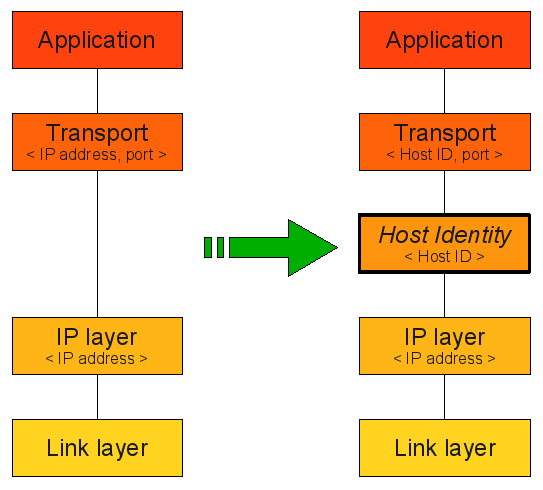
HIP solves one of the basic problems of the Internet; the conflation of location and identity for hosts. Along with fixing the issue, HIP also provides solid and adaptable security between OSI layers 3 and 4, giving it unique properties. Critical has been an adopter of HIP for many years attempting to use it in every project possible. Most recently HIP was used in a subcontracting job for a start up to secure Tahoe-LAFS as well as in our baseline ITS system. This marriage of technologies has resulted in our DIG:DSG product. We are active within the HIP community (which extends into its IETF working group) by helping with open source implementations and writing drafts to update the HIP standard.
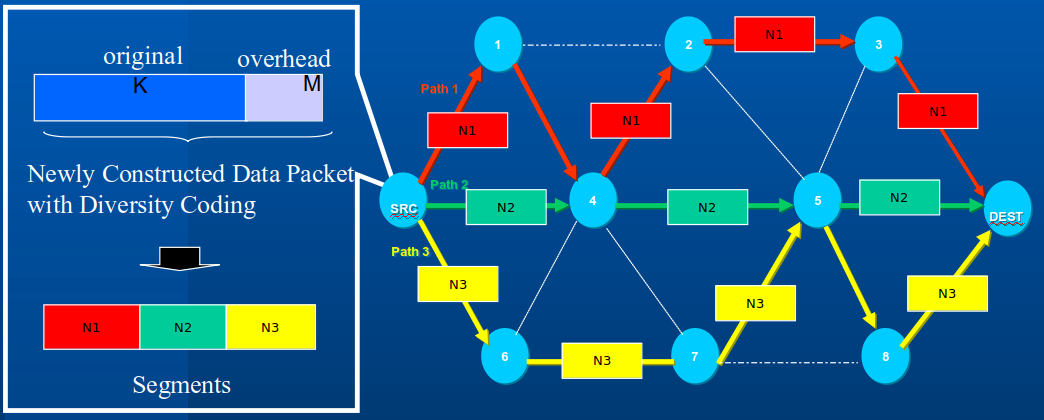
Critical's history in CMR is focused on being link agnostic across various media (VHF line of sight, HF beyond line of sight, SATCOM) that can have any of the following characteristics; high latency, low data rate, high error rate, asymmetric and intermittent connectivity and highly contested environments. Our CMR was designed to use our DTN technologies on a packet-by-packet basis, as opposed to file by file basis, over the various dissimilar links to provide reliable connectivity. PUMA was designed to use our CMR technologies, link health heuristics and path performance to anticipate link degradation or loss and auto-route around the disruption.
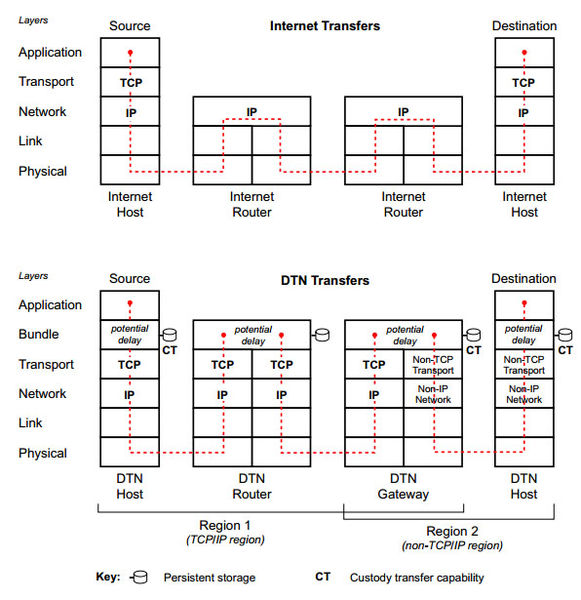
Critical was doing DTN before it even was named by the IETF research group. Our old Application Traffic Controller (ATC) project for naval submarines brought IP connectivity to a place deemed unreachable at the time, utilizing the store and forward mechanics of DTN. We are still involved in this area being active members of the DTN working group at IETF and applying DTN where it helps in Quality of Service.
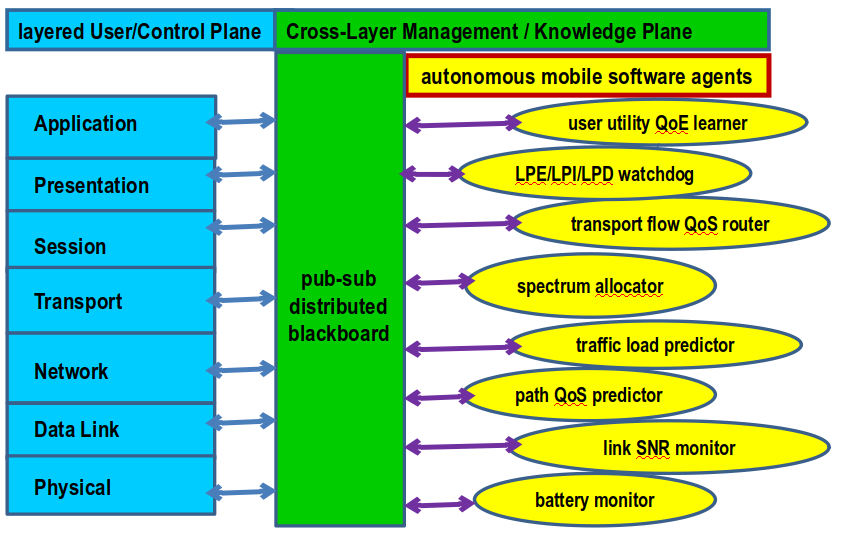
CTI has designed and instantiated a number of productive and cognitive networking tools and code, including the Predictive Unicast Multipath Algorithm (PUMA) for 2009’s Navy LCS/UUV Adaptive Remote Sensor Communications program, 2011’s Evolutionary Learning with Information Theoretic Evaluation of Ensembles (ELITE2) framework, and 2012’s CYber, Cross-Layer Optimized, Publish / Subscribe (CYCLOPS) framework for the USAF AFRL RI’s Cognitive networking program.
Critical's main technology focus in distributed storage is the use of Tahoe Least Authority File Storage (Tahoe-LAFS). An open source project the benefits and use of such a technology is a powerful for many applications. Our main product, the DIG:DSG, utilizes Tahoe-LAFS to protect motionless data along with HIP to secure its transport.
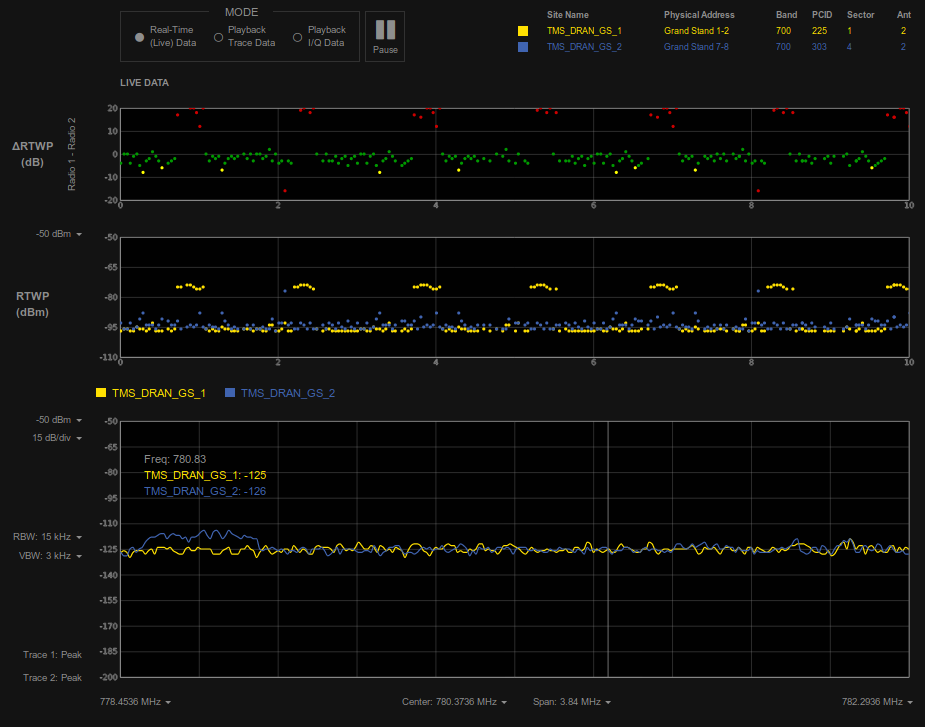
Our team is well versed in RF technologies, with most employees holding valid Amateur Radio licenses of General Class or higher. Our most current work in this field was being subcontracted by QoScience, LLC to create a remote spectrum analyzer for LTE networks. A demo of the RANalyzer is still up today at our facility and is accessible from any Chrome web browser by going here. Future models of the DIG are planned to use Software Defined Radios (SDRs) to enable easy remote viewing of spectrum to give users spectrum awareness.
Our company has done many things over the past 25 years, so much so that we can't highlight all of them. To see some of our older work, please contact us to learn more!
© Critical Technologies Inc. All rights reserved. | Design by TEMPLATED.